 |

We ran a set of micro benchmarks on Snapdragon and measured the latency of each operation in order to evaluate the various overheads associated with our security scheme. All the latency benchmarks were run on a collection of 700 files, each of size 4 KB. In each benchmark, a fixed filesystem operation (e.g., read or chmod) was performed on each of the files in a randomized order. For the read and write cases, the metadata server, simulated NAD, and client driver were instrumented to report the time spent in fine-grained sub-operations.
 |
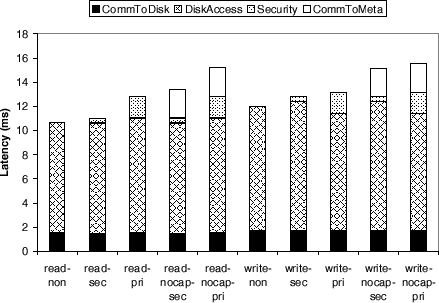
Figure 8 shows the latency breakdown of the read and write operations with empty and synchronous write-through caches respectively. The physical disk access time averaged 9.3 ms for reads and 10.2 ms for writes. The MAC computation overhead was 0.4 ms and the encryption overhead was 1.4 ms. The disk-communication latency for all operations was 1.6 ms. If the client needs to request a capability for an operation, it requires an additional round trip from the client to the metadata server, which costs 2.3 ms. If a client attempts to use a revoked capability (not shown), it will get a rejection from the disk, which costs an extra 1.8 ms (secure setup) or 2.5 ms (private setup).
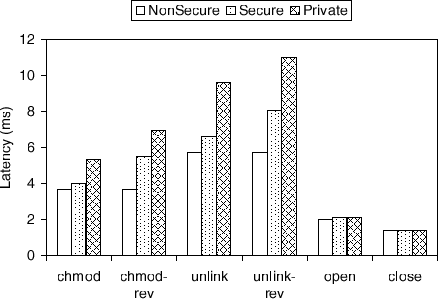 |
Figure 9 shows the latency of metadata
operations. The chmod operation involves a round trip from the
metadata server to the simulated NAD that requires MAC computation,
while the unlink operation involves multiple such trips because ext2's
unlink code writes multiple disk blocks. The open operation involves
both MAC computation (to compute the secret ![]() ) and encryption of the
capability, whether or not encryption for privacy is used. For
operations that do not require revocations, the overhead for access
control is less than 1 ms and the overhead for privacy is less than
3 ms. The operations involving revocations (i.e., chmod-rev and
unlink-rev) require an additional round-trip from the metadata server
to the disk, roughly 1.4 ms.
) and encryption of the
capability, whether or not encryption for privacy is used. For
operations that do not require revocations, the overhead for access
control is less than 1 ms and the overhead for privacy is less than
3 ms. The operations involving revocations (i.e., chmod-rev and
unlink-rev) require an additional round-trip from the metadata server
to the disk, roughly 1.4 ms.
In summary, access control (i.e., MAC computation and replay detection) increases the latency of reads and writes by less than 0.5 ms (5%); encryption an additional overhead of 1.4 ms; and capability revocation increases the latency of read or writes latency by roughly 2.3 ms. For metadata operations, access control costs can cost 1 ms and privacy can cost 3 ms for certain operations.