![[*]](../../../graphics/buttons/cross_ref_motif.gif)

To address these problems we will use the mechanisms provided by the
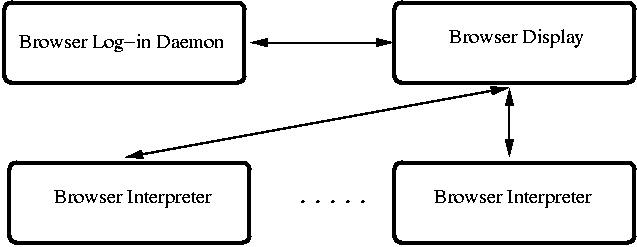
SubOS-capable operating system, as well as a modular Web browser architecture.
We divide the Web browser into three parts, according to its functionality.
The first part is responsible for down-loading objects over the network,
the second is responsible for displaying the content, and the last is a set
of helper applications/interpreters used to process the content of the
down-loaded objects. The design is presented in Figure ![[*]](../../../graphics/buttons/cross_ref_motif.gif)
 |
We decided against using an existing Web browser since that would
require significant modification to its architecture. Down-loading and
authentication of objects could be easily achieved by using a proxy, however
execution of embedded code in HTML web pages would be a lot more challenging,
since it would have to execute in a separate address space to maintain
its security properties, as we discussed in Section ![[*]](../../../graphics/buttons/cross_ref_motif.gif) .
.