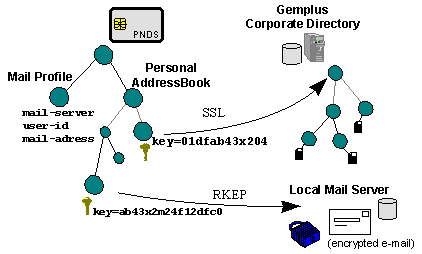
Figure 6 - Example of a PNDS-based Security Architecture

Security should play a central role in the Personal Naming and Directory Service. However, scope of this paper is only limited to decribe PNDS itself and its integration into distributed systems. Therefore, we focuse our discussion on presenting only some possible mecanisms to deploy security within the PNDS. We consider the following security concerns :
Access to the PNDS information is currently permitted after typing the right PIN code, nothing is supplied otherwise. However a PNDS may consist of several services for various external applications with different types of accessing users. Access to pieces of information may require a specific authorisation.
A first approach of this problem may lead to identify two kinds of users, each one having a different level of access privileges to read/write parts of the PNDS :
Different PIN codes can be assigned to different privilege levels, and access conditions have to be set and verifyied at the context level .
The other perspective concerns the overall security of distributed applications. Extensive security can be implemented for naming and directory services. PNDS can act as a keys and certificates provider, and is able to use cryptographic features provided as part of the smartcard operating system.
Possible roles of PNDS in the security of distributed application over the Internet are illustrated on figure 6. The Secure Socket Layer (SSL) is used to authenticate users to other naming servers on the network (i.e., referrals), while the Remote Keys Encryption Protocol (RKEP) [ref 20] is used to secure content (i.e., cipher/decipher mail folders). Part of such a security architecture has already been demonstrated by Gemplus in the Vault prototype [ref 21].

Figure 6 - Example of a PNDS-based Security Architecture