|

The last two decades of network security research have demonstrated that attackers are continuously evolving, exploring creative ways to exploit systems, and targeting new technologies and services as they emerge. Indeed, the widespread use of email brought spam and email-viruses; broadband connectivity was followed by the rise of rapid self-propagating worms; while the growing use of online personal services and electronic commerce resulted in sophisticated personal data theft attacks, including phishing. Such trends suggest that any technology that reaches some kind of critical mass will attract the attention of attackers.
At the same time, modern attacks such as worms, spam, and phishing exploit gaps in traditional threat models that usually revolve around preventing unauthorized access and information disclosure. The new threat landscape requires security researchers to consider a wider range of attacks: opportunistic attacks in addition to targeted ones; attacks coming not just from malicious users, but also from subverted (yet otherwise benign) hosts; coordinated/distributed attacks in addition to isolated, single-source methods; and attacks blending flaws across layers, rather than exploiting a single vulnerability. Some of the largest security lapses in the last decade are due to designers ignoring the complexity of the threat landscape.
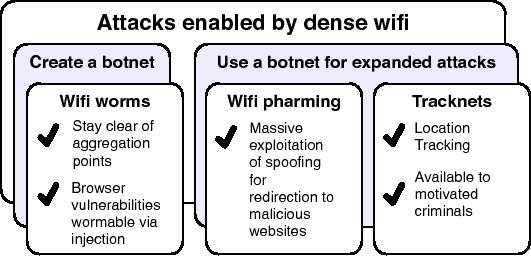
The increasing penetration of wireless networking, and more specifically wifi, may soon reach critical mass, making it necessary to examine whether the current state of wireless security is adequate for fending off likely attacks. This paper discusses three types of threats that seem insufficiently addressed by existing technology and deployment techniques. The first threat is wildfire worms, a class of worms that spreads contagiously between hosts on neighboring APs. We show that such worms can spread to a large fraction of hosts in a dense urban setting, and that the propagation speed can be such that most existing defenses cannot react in a timely fashion. Worse, such worms can penetrate through networks protected by WEP and other security mechanisms. The second threat we discuss is large-scale spoofing attacks that can be used for massive phishing and spam campaigns. We show how an attacker can easily use a botnet by acquiring access to wifi-capable zombie hosts, and can use these zombies to target not just the local wireless LAN, but any LAN within range, greatly increasing his reach across heterogeneous networks. Last but not least, we discuss the use of Tracknets, city-wide wifi botnets for unauthorized tracking of user location and behavior.
All three types of attacks, illustrated in Figure 1, are specific to wireless networks, and are based on the premise of dense wifi network deployment in urban settings. While most of the underlying vulnerabilities have been widely known for years, the amplifying power of densely deployed wifi networking has a profound impact on both the feasibility and the magnitude of the threats, suggesting that their importance may have been grossly underestimated. For instance, the susceptibility of open wireless LANs to spoofing has been well documented, but the need to be in physical proximity to the victim may have deterred the wider use of this attack so far. The ability to launch such attacks remotely is much more attractive, and can be scaled up by the use of coordination and a botnet infrastructure.
As a result of underestimating these threats, no countermeasures are currently implemented. The mechanisms needed to thwart these attacks are in most cases either available but not actively used, or not available but relatively easy to implement. The fact that such mechanisms are not used is of particular concern. For instance, 802.11i security mechanisms have been available for several years, and would address a large part of the problems described, but unfortunately they are currently not used by enough users. Similarly, the encryption of of MAC addresses would significantly increase the work-factor for Tracknets, but leaving the MAC addresses exposed was not deemed as a serious enough problem by the 802.11i group. Related to the worm problem, content-based filtering is widely used and intrusion prevention is a mature technology, yet to the best of our knowledge, it has not been employed in access point wireless-to-wireless forwarding Raising awareness on the threats, using convincing, experimental evidence, is therefore at least as important as exploring and implementing possible defenses.
The main focus of this paper is in quantifying these threats, specifically in metro-area wireless networks. We rely primarily on publicly available maps of wireless access point locations, also known as wardriving maps, and attempt to derive estimates on the feasibility and effectiveness of the attacks using measurements and simulations. These estimates paint a grim picture on the exposure of current wireless networks to such attacks, and indicate that the risks are further increased as wireless penetration continues to grow as predicted.
We also explore possible remediation strategies, most of which we have implemented and tested experimentally. In some cases, the defenses we have considered are just a matter of engineering, such as retrofitting reactive worm defense hooks and filtering capabilities in wifi gear. In other cases, countering the threat required novel techniques, such as those for detecting and preventing different variants of the basic spoofing attack - several such variants were discovered while pondering about possible defenses, and how attackers might try to circumvent them.
While some of these techniques would become redundant if 802.11i is widely deployed, we cannot rest on the assumption that such deployment will happen anytime soon, particularly in light of usability concerns. For example, none of the recently announced municipal wireless initiatives that we are aware of employ any form of protection, most likely due to the current perception of the risks of open wireless as well as the cost of managing accounts and passwords for large number of users - in one instance, 100,000 users and around 9M annual visitors. Furthermore, the choice of running an open wireless network may not always be a matter of ignorance or complacency, but a concious choice; for example, to provide network access to guests, backup connectivity to neighbors, etc [26]. Whether temporary or long-term, we believe that our supplementary defense techniques are useful for mitigating at least part of the threat.