 |

 |
In this section, we describe ROAM, which provides an end-to-end
architecture for Internet host mobility on top of ![]() .
.
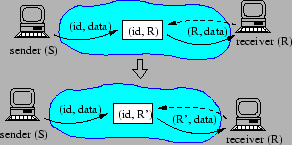
Achieving host mobility using ![]() is straightforward. A mobile host
that changes its address from
is straightforward. A mobile host
that changes its address from ![]() to
to ![]() as a result of moving from
one subnetwork to another can preserve end-to-end connectivity by
simply updating each of its existing triggers from
as a result of moving from
one subnetwork to another can preserve end-to-end connectivity by
simply updating each of its existing triggers from ![]() to
to ![]() , as shown in Figure 3.
, as shown in Figure 3.
ROAM exhibits the following desirable properties:
Efficient routing. ROAM takes into account the mobility pattern
of the end-hosts to improve ![]() 's ability to provide low
latency stretch
(see Section 4.1).
's ability to provide low
latency stretch
(see Section 4.1).
Efficient handoff. ROAM implements fast handoff and multicast-based handoff to reduce packet loss during handoffs (see Section 4.2).
Fault tolerance. Since triggers are periodically refreshed, ROAM recovers gracefully from server failure. If a server fails, the triggers stored at that server are inserted at another server the next time they are refreshed.3 Section 7.1.4 evaluates ROAM's robustness through simulation.
Simultaneous mobility. The sending and receiving hosts can move
simultaneously while ![]() serves as an anchor point for the two sides
of the communication channel.
serves as an anchor point for the two sides
of the communication channel.
Location privacy. ROAM allows end-hosts the flexibility of choosing triggers to not reveal any location information. Section 4.3 discusses the tradeoffs between location privacy and routing efficiency.
Personal/session mobility. Unlike Mobile IP, ROAM allows a user to redirect a new session or migrate an active one from one application or device to another when a better choice becomes available (see Section 4.4).
Next, we describe efficient routing, efficient handoff, location
privacy, and personal/session mobility in more detail. The key to
achieving these properties is the ability of end-hosts to control
the location of a trigger in ![]() . Since fault tolerance and simultaneous
mobility follow directly from
. Since fault tolerance and simultaneous
mobility follow directly from ![]() 's properties, we do not discuss them
here.
's properties, we do not discuss them
here.