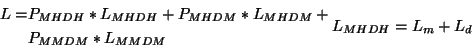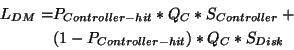![]()
![]()
![]()
Next: Experimental
Analysis Up:
Polus : Growing Storage Previous: Meta-level operations
Experimental Setup
In the
experimental setup, a SAN file system simulator is being used as the managed
system. For the management software, we use an implementation of the Polus toolkit and compare it with its rule-based ECA
counterpart. The Polus toolkit is built using ABLE (
The entities within the SAN file-system simulator are similar to those introduced in Section 2. The cost of atomic operations used in the simulator are shown in table 1. The simulator models the following actions that are invoked by the management software via actuators: Pre-fetch size tuning, Data replication, Backup and Clean-delay interval. I/O operations within the SAN file system are invoked by the client and can have multiple possible paths, depending on whether the data is cache or not. The simulator considers the following paths:
MHDH: Metadata and data hit in the client
MHDM: Metadata hit and data miss in client
MMDM: Metadata and data miss in the client
The
summation of each of these probabilities of the invocation paths ![]()
The average I/O latency is given by:
|
|
|
|
The
values for probabilities such as ![]() , and
, and ![]() are modeled by representing the caches
as finite sized-arrays and keeping track of data blocks in the elements.
Similarly, the average queue depth such as
are modeled by representing the caches
as finite sized-arrays and keeping track of data blocks in the elements.
Similarly, the average queue depth such as ![]() are
actually modeled by using service time to complete each request.
are
actually modeled by using service time to complete each request.
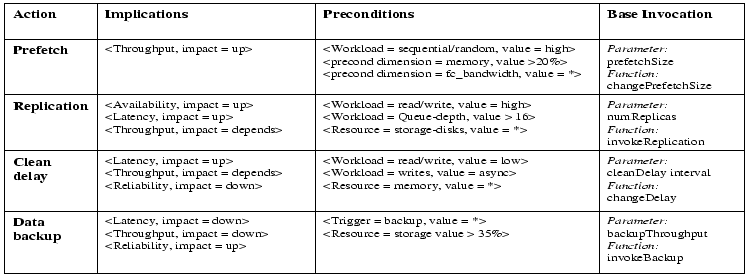
Each action is modeled to reflect its impact on the invocation path, system resources and changes in the workload characteristics (table 2). To activate the actions in the file system simulator, specifications are fed into Polus and rule-based management. The specifications for a rule-based system consist of ECAs that describe the system-behavior for different system-states. The ECA specifications in this example run into 7 pages (76 rules). The exact Polus specifications that are fed are given in figure 8.
![]()
![]()
![]()
Next: Experimental Analysis Up:
Polus : Growing Storage
Previous: Meta-level
operations