
Next: The Browser Architecture
Up: SubOS-enabled Operating Systems
Previous: SubOS-enabled Operating Systems
As we mentioned earlier in Section ![[*]](../../../graphics/buttons/cross_ref_motif.gif) , every time the system
accepts an incoming object it associates a sub-user id with it,
depending on the credentials the object carries.
The sub-user id is permanently saved in the Inode of the file that holds
that object, which is now its immutable identity in the system
and specifies what permissions it will have.
It has essentially the same functionality as a UNIX user id.
One can view this as the equivalent of a user logging in to the system.
, every time the system
accepts an incoming object it associates a sub-user id with it,
depending on the credentials the object carries.
The sub-user id is permanently saved in the Inode of the file that holds
that object, which is now its immutable identity in the system
and specifies what permissions it will have.
It has essentially the same functionality as a UNIX user id.
One can view this as the equivalent of a user logging in to the system.
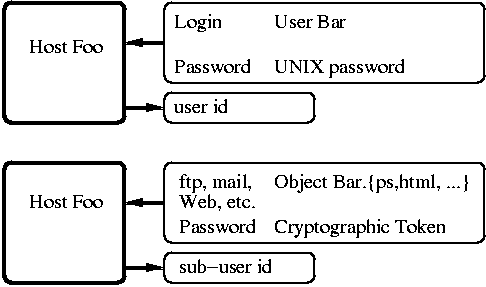
Figure ![[*]](../../../graphics/buttons/cross_ref_motif.gif) shows the equivalence of the two mechanisms.
In the top part of the figure we see the regular process of a
user Bar logging in a UNIX system Foo and getting a user id.
In the same way, objects that enter the
system through ftp, mail, etc., ``log in'' and
are assigned sub-user id's based on their (often cryptographically-verified)
source.
shows the equivalence of the two mechanisms.
In the top part of the figure we see the regular process of a
user Bar logging in a UNIX system Foo and getting a user id.
In the same way, objects that enter the
system through ftp, mail, etc., ``log in'' and
are assigned sub-user id's based on their (often cryptographically-verified)
source.
Figure:
In the top part of the Figure we see the regular process of a
user Bar logging in a UNIX system Foo and getting a user id.
In the same way objects that enter the
system through ftp, mail, etc., ``log in'' using a cryptographic token, and
are assigned sub-user id's.
 |


Next: The Browser Architecture
Up: SubOS-enabled Operating Systems
Previous: SubOS-enabled Operating Systems
Sotiris Ioannidis
4/28/2001
![[*]](../../../graphics/buttons/cross_ref_motif.gif) shows the equivalence of the two mechanisms.
In the top part of the figure we see the regular process of a
user Bar logging in a UNIX system Foo and getting a user id.
In the same way, objects that enter the
system through ftp, mail, etc., ``log in'' and
are assigned sub-user id's based on their (often cryptographically-verified)
source.
shows the equivalence of the two mechanisms.
In the top part of the figure we see the regular process of a
user Bar logging in a UNIX system Foo and getting a user id.
In the same way, objects that enter the
system through ftp, mail, etc., ``log in'' and
are assigned sub-user id's based on their (often cryptographically-verified)
source.

