 |

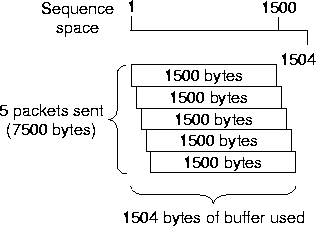
Luckily, we observe that TCP implementations trim packets that overlap the sequence space that has already been received. Consequently, if a packet arrives that overlaps a previously received packet, then the receiver will only buffer the portion that occupies ``new'' sequence space. By explicitly overlapping the sequence numbers of our probe packets we can map each large packet into a single byte of sequence space, and hence only a single byte of buffer at the receiver.
Figure 4 illustrates this technique. The first 1500 byte packet is sent with sequence number 1500, and when it arrives at the target it occupies 1500 bytes of buffer space. However, the next 1500 byte packet is sent with sequence number 1501. The target will note that the first 1499 bytes of this packet have already be received, and will only use a single byte of buffer space. Using this technique we can map every additional packet into a single sequence number, eliminating much of the buffering limitation. This technique only allows us to send bursts of data in one direction - towards the target host. Coercing the target host to send arbitrarily sized bursts of data back to the source is more problematic since TCP's congestion control mechanisms normally control the rate at which the target may send data. We have investigated techniques to remotely bypass TCP's congestion control [SCWA99] but we believe they represent a security risk and aren't suited for common measurement tasks.