|
| |||||||||||||||||||||||||||||||||||||||||||||||||||

| ||||||||||||||||||||||||||||||||||||||||||||||||||||
|
USENIX Technical Program - Paper - Smartcard 99
[Technical Program]
(*) This paper reports on work done at the IBM Zurich Research Laboratory, Ruschlikon, Switzerland. Abstract Existing payment smartcards developed for traditional point-of-sale transactions are being considered for use in Internet transactions. Such solutions have been suggested as alternatives to using payment protocols more specifically designed for Internet payments (such as SET [8]) but often lacking smartcard support. In this paper, we analyze EMVā96 [7], a representative example of an existing payment smartcard specification. We investigate which security requirements for an Internet payment system can and cannot be met when using EMV for Internet payments. We suggest possible modifications that can enhance the security of an Internet payment scheme based on EMV. 1. IntroductionWith the growing use of the Internet for commercial transactions, there has been much effort in developing systems and protocols for securing payments on the Internet. A prominent example of such a protocol is the Secure Electronic Transaction (SET, [8] ) protocol. It is, however, not designed with smartcard support in mind. Current implementations require the customer to make SET transactions from a fixed, trusted personal computer. A secure SET implementation on a smartcard for use with public (and untrusted) terminals would require the smartcard to store the userās account data and cryptographic keys as well as the SET client implementation, which is not feasible with current smartcard technology.The lack of portability of Internet-specific systems such as SET has caused the payment industry to look at the possibility of using existing debit and credit payment smartcards for Internet payments. A standard in this area is the EMVā96 Specification [7] , which describes the functionality required by such smartcard-based payment systems. The objective of this paper is to discuss the potentials and restrictions of using EMV payment cards for debit and credit payments over the Internet. In Section 2 we formulate a set of general security requirements for smartcard-based debit and credit Internet payments. After summarizing EMVā96 security mechanisms in Section 3, we analyze in Section 4 the security properties of using EMV Īas isā for Internet payments, by checking the resulting protocols against the formulated requirements. Since the Internet scenario differs from the scenario assumed by EMVā96, these protocols exhibit a number of vulnerabilities. In Section 5, we finally discuss possible mechanisms to increase the security of using EMV in the Internet scenario. 2. Model and Security Requirements for Smartcard Internet PaymentsOur model of a generic Internet payment system (Figure 1) consists of a customer and a merchant who exchange money for goods or receipts, and at least one financial institution linking electronic payments to the transfer of "real money" [1]. Customer and merchant communicate over an open network (the Internet) with each other and with their banks (issuing bank and acquiring bank, respectively). During a transaction, actual connectivity may be limited to certain subsets of players. In a typical online purchase scenario, the customer only has a connection to the merchant, and communicates indirectly with his issuing bank (e.g., through an authorization message sent to the merchant and forwarded by the merchant to acquiring and issuing banks). The underlying communication model, however, does not influence the security requirements stated in the following. Before formulating security requirements for a payment
transaction, we need to make a number of assumptions about trust relations
and liability distributions between the parties involved:
A number of requirements deal with proof of authorization of the transaction by an authorizing party to a verifying party. This is achieved by an authorization message containing a non-forgeable cryptographic proof of authentication by the authorizing party of critical transaction-related data, satisfying the following properties:
3. Security Mechanisms Provided by EMVThis section gives an overview of EMVā96 security mechanisms securing transaction flows. Mechanisms such as card and terminal risk management are not discussed here. For a detailed description of security mechanisms provided by EMVā96 we refer to [7] .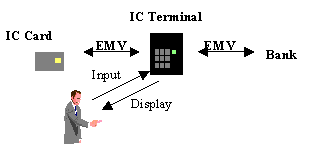 Figure 2 shows the general EMV POS scenario of an IC (Integrated Circuit) terminal interacting with an IC card, with the human user presenting the card, and with the bank. (The actual EMV functionality for authorizing transactions resides with the issuing bank. In this analysis, we make abstraction of the distinction between the issuing bank and the merchantās acquiring bank. )
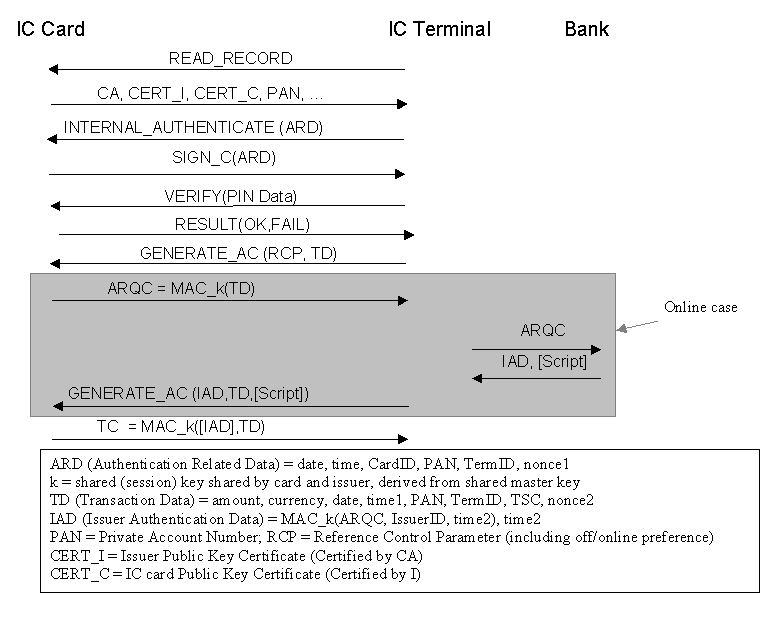
Figure 3. Model EMV Transaction Flow 3.1. Public-key based authentication of IC card to IC terminalThe first four messages exchanged implement the Dynamic Data Authentication (DDA) authenticating the card to the terminal using a public-key based challenge-response protocol. The READ_RECORD command returns the necessary Certification Authority (CA) identifier and public-key certificates needed by the terminal to authenticate the cardās public key in CERT_C. CERT_C is certified by the issuer and can be verified using the issuerās public key in CERT_I, which in turn is certified by the CA and can be verified using the CAās public key known to the terminal. The actual challenge-response authentication is then executed by the terminal issuing an INTERNAL_AUTHENTICATE command containing authentication-related data (ARD), and the card responding with a signature over this data using its private signature key.For cards without digital signature capability, EMV also provides the Static Data Authentication mechanism using static card data signed by the Issuer. 3.2 Cardholder VerificationEMV supports online (PIN sent to and verified by the bank) and offline (PIN verified by the card) PIN verification; the exact method supported by the card is read by the terminal with the initial READ_RECORD. Offline PIN verification is executed by the terminal issuing the VERIFY command, containing the PIN data entered by the user; the cardās response indicates success or failure. The response is not cryptographically authenticated.3.3. Shared-key based application cryptograms and off- or online processingThe GENERATE_AC command, including Transaction Data (TD), triggers the card to produce a cryptogram that can be verified by the issuer. If both card and terminal agree on completing the transaction offline (based on both entitiesā risk management policies) the card returns a TC (Transaction Certificate) approving the transaction. If either card or terminal want to continue online, the card produces an ARQC (Authorization Request Cryptogram), which the terminal passes on to the bank in an online authorization request. If verification is successful, the bank returns an authorization response message containing Issuer Authentication Data (IAD) and possibly a command script to be delivered to the card. The terminal then issues the second GENERATE_AC command including the IAD and the command script.ARQC, TC and IAD are authenticated using MACs (Message Authentication Codes). These are generated by 64-bit block ciphers using a session key k derived from a master key shared by the card and the issuer. The issuer can verify both ARQC and TC; in the online case the card verifies the IAD in the second GENERATE_AC command and thereby authenticates the issuerās response. The terminal triggers the generation and verification of these cryptograms but cannot verify them. 4. EMV Payments in the Internet ScenarioIn the remainder of this paper, we analyze if and how EMV cards can be used for secure Internet payments.The scenario (Figure 4) depicts a customer using his or her EMV card for online purchases from a PC that has a card acceptance device (reader) attached to it. The merchant still acts as the EMV terminal, issuing and receiving EMV commands and responses, but now communicates with customer and bank over the Internet. 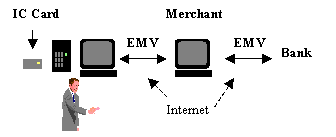 PIN verification deserves some special attention. While, in the POS scenario, the terminal secures the transaction by making sure the PIN is verified correctly (by card or bank), PIN verification in an Internet setting can and should no longer be controlled by the merchant:
In the following paragraph we analyze the security of these two scenarios by checking them against the security requirements defined in Section 2. Table 1 also summarizes the results of this analysis.
The results of the analysis in Table 1 show a majority of unsatisfied requirements (N) without a distinction between offline and online scenarios. This is a result of the EMV specifications being developed for the POS scenario where the EMV terminal is under some control by the merchant (sometimes also bank), the purchase is performed face-to-face and merchant and bank communicate over secure connections. We shortly list and illustrate these assumptions.
4.1. No payment guarantee for the merchantThis is probably the most serious problem: without a payment guarantee the merchant may lose money when delivering goods which are not paid for afterwards.
4.2. No merchant authorizationThe absence of an explicit authorization of the transaction by the merchant means that an attacker may impersonate a real merchant to both customer and bank, and conduct a successful transaction on behalf of the real merchant who might not even be aware. This vulnerability can be exploited also by dishonest customers and merchants: a merchant can repudiate a transaction afterwards, claiming the above attack scenario has occurred; a dishonest customer may exploit the lack of merchant authorization by intercepting and modifying the transaction data on the merchant to bank channel. In the attack scenario as well as the dishonest merchant scenario, the customer does not get the ordered goods and has to claim refund while in the last scenario the merchant does not receive the expected payment for possibly delivered goods.4.3 No merchant-to-customer authentication and certificationFor debit or credit payments the danger for the customer caused by lack of merchant authentication is limited: the customer can only lose money to a legitimate merchant if we assume that the bank only clears payments for legitimate merchants. The absence of a merchant-to-customer (M-C) authentication mostly reinforces the danger caused by the absence of a merchant-to-bank (M-B) authorization, in the sense that a fully complete, normal and legitimate payment to M can take place without M being involved in any stage of the EMV protocol. On the contrary, a reasonable protection can be achieved if at least one of the two, M-C authentication or M-B authorization, is provided. Then either the customer or the bank can verify whether M is the merchant corresponding to the TermID in the ARQC or TC. If there is M-B authorization (at least during clearing), but no M-C authentication then it only remains critical that the customer might communicate with a different merchant than intended.4.4. No receipt for the customerNot receiving a payment receipt is mainly critical for the customer if s/he buys goods to conditions which change rapidly (e.g. stocks or shares). Especially in the offline protocol, the customer does not have any proof of having bought something to specified conditions before the actual clearing is performed and s/he has received his or her statement of account. This can cause a loss of goods, opportunities, or money to the customer if the merchant denies certain conditions.Note that within EMV it is impossible to simultaneously provide the merchant with a payment guarantee and the customer with a receipt because one message always has to be sent last. A simultaneous payment guarantee and customer receipt could be provided if the protocol were embedded in some fair-exchange protocol (such as [2]), which is out of the scope of EMV. 5. Mechanisms to Add Security when Using EMV over the InternetWe now discuss the benefits of different mechanisms which can secure EMV when used over the Internet. The protocol vulnerabilities of Ībareā EMV over the Internet relate to the absence of authorization of certain messages, and to the absence of authentication and certification of the merchant to the customer. We first analyze the merits of using a transport-layer mechanism such as SSL to secure the communication channels used, a solution which doesnāt impose any changes on the EMV infrastructure. Given the limited improvements achieved with this approach, we then recommend some modifications to the EMV infrastructure that might allow a more secure use of EMV for Internet payments.5.1. Securing communication channelsTo the extent that SSL can provide initial authentication between communicating parties and integrity and/or confidentiality protection of the ensuing dialogue, it can provide a reasonable degree of protection against attacks by outsiders, under the condition that all parties involved adequately secure their systems. However, as discussed in the following paragraphs, SSL cannot provide the necessary authorizations we discussed before that are needed to protect parties against dishonest insiders.SSL cannot authenticate individual EMV messages, rather it integrity-protects a data stream, which in addition could carry data generated by applications other than EMV. It secures the data using a shared session key which is temporary and cannot be tied to a specific party, except by its communication partner, and then only during the existence of the connection. Obviously, SSL Īauthenticatedā messages or data streams can never have any authenticating value to a third party, regardless of trust assumptions of this third party. (One could of course argue whether this is the case for EMV ARQCs or TCs. But given the assumed tamperproofness of the cards, and possibly certified security of a bankās systems, EMV ARQCs or TCs may be considered by a third party as non-repudiable evidence.) The authorizing value they have to the receiving party during the connection depends entirely on the receiverās trust in the senderās system and the senderās honesty. In a model where banks and merchants trust each other, this may suffice to add a weak authorization value to EMV messages exchanged between them; less clear is the authorization value for messages exchanged between customer and merchant. Specifically, in the offline scenario, it cannot provide a customer-authorized payment guarantee for the merchant. Summarizing, we can say that SSL, under certain conditions, can add reasonable security against outsider attacks, but does not provide the authorization of EMV messages necessary to protect against dishonest insiders (or against honest insiders using insecure systems). In the next subsections, we suggest two modifications to EMV which can help towards solving these problems. 5.2. Signed authorization responseIn the online scenario, an undeniable payment guarantee for the merchant may be provided by the (issuing) bank signing the authorization response message with its private signature key. The authorization response message becomeswhere SIGN_I() stands for a signature with message recovery using the (issuer) bankās private signature key. This message can then be verified by the merchant (who already has obtained the issuerās public key during DDA) and can be submitted to the issuer again for final clearing. The advantages of this extension are:
5.3. Public-key Transaction Certificate (TC)Another proposed change to the EMV specifications is the use of a public-key signature also for TC generation. The TC becomessigned using the cardās private key. A public key-based TC is verifiable by the merchant and can be considered as a payment guarantee depending on contract terms between merchant and acquirer (which may require certain risk management measures by the merchant). A public-key signed TC seems to be a natural extension given that DDA-capable cards already have the signature generation capability. However, in order to support this extension, message formats for cryptogram generation need to be changed, which may have a major impact on the whole EMV infrastructure and poses challenges related to backward compatibility. Security gains that can be achieved by using a public-key based TC are:
5.4. Merchant authenticationChanges proposed in 5.2 (online payments only) or 5.3 (especially important for offline payments) can greatly improve the security of the respective EMV-Internet scenarios. Vulnerabilities remain, primarily related to the lack of authentication and authorization of the merchant to both customer and bank. Closing these holes in a rigorous way by providing merchant authentication in EMV largely impacts the EMV infrastructure which currently does not allow for the storage of secret keys in merchant terminals. However, to the extent that the keys stored need not be system-wide symmetric keys but rather the merchantās own private signature key for authentication to bank and/or customer, we believe that such a modification can only strengthen overall security. Such a change first of all allows the merchant to sign the authorization request message, providing secure authorization by the requesting merchant. It also allows merchants to authenticate to the card and to deliver a signed payment receipt to the customer which in the offline case is the only means for the customer to get a receipt (other than an after-the-fact account statement). Since cards with signature verification capability are not likely to be used soon, the signature verification could be done in the trusted card reader (or eventually, in the PC software).6. Related WorkThe principle of using existing payment smart cards to secure Internet transactions has been applied in recent projects such as the e-COMM [4] and C-SET [6] projects in France. Both integrate shared-key based Transaction Certificates from existing EMV-like banking cards within SET or SET-like protocols. In this paper, rather than proposing a specific solution, we have tried to give a comprehensive and systematic overview of the security features and limits of a variety of related solutions, and hope it can be applied in the evaluation or design of similar systems.7. ConclusionThe use of EMV Īas isā over the Internet has major (and unacceptable) security shortcomings. Securing the communication channels between the different parties (customer, merchant, bank) using secure communication protocols can prevent mainly outsider attacks. However it does not solve the inherent lack of authentication in the EMV protocol. Therefore we propose a number of EMV extensions which can increase security in the Internet setting.The most challenging is the EMV offline scenario, where only the use of a public-key based Transaction Certificate provides appropriate security to the merchant. This scenario is particularly important if EMVā96 is used for purse (e-cash) applications. Online EMV authorization in an Internet setting, though currently insecure because of merchant as well as bank impersonation attacks, can be made more secure by digitally signing authorization requests and responses. Lack of initial authentication and certification of the merchant to the customer is a vulnerability only to be solved by extending the EMV infrastructure with terminal-to-card (alternatively, terminal-to-reader or terminal-to-userās PC) dynamic authentication. In the absence of terminal authentication, software-based mechanisms (e.g. SSL server-to-client authentication) can be put in place to thwart the biggest risks of outsider attacks. 8. AcknowledgmentThe authors thank Michael Waidner for his helpful comments and suggestions.9. References |
|
This paper was originally published in the
Proceedings of the 1st Workshop on Smartcard Technology, May 10-11, 1999, McCormick Place South Chicago, Illinois, USA
Last changed: 18 Mar 2002 ml |
|