
Next: Acknowledgements
Up: Toward Speech-Generated Cryptographic Keys
Previous: Related Work
The viability of (re)generating strong cryptographic keys from voice
utterances remains unproven. While we believe that the work presented
in this paper offers steps toward achieving this goal and evidence
that it can be reached, some critical advances are still required.
Notably, our analyses using 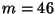 in [16] and
in [16] and 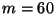 here
are insufficient for security as required in commercial applications,
and our future work will continue to focus on reaching
here
are insufficient for security as required in commercial applications,
and our future work will continue to focus on reaching 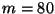 or
higher. More extensive user trials to evaluate the entropy of users'
distinguishing features is also needed. And, there remain numerous
open questions as to how to tune an implementation of our approach in
practice. The analysis of Section 5 hides many
parameters from view, and the relationship between these parameters,
security and usability need to be further explored.
or
higher. More extensive user trials to evaluate the entropy of users'
distinguishing features is also needed. And, there remain numerous
open questions as to how to tune an implementation of our approach in
practice. The analysis of Section 5 hides many
parameters from view, and the relationship between these parameters,
security and usability need to be further explored.
Subsections
fabian
2002-08-28
