

Next: Adversaries and attacks
Up: Model and System Architecture
Previous: Security design goals
We will use the following terminology for the parties involved in
VarietyCash.
In a typical transaction there would be three parties involved:
the payer, the payee, and the bank or e-money
server. However, we would like to be more specific than that:
- Participant - A generic name for a party involved in the system.
- Issuer (
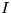 ) - Party who issues coins.
) - Party who issues coins.
- Coin-holder (
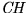 ) - A party who holds coins or has the
potential to do so.
) - A party who holds coins or has the
potential to do so.
- Payee (
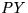 ) - A party who is willing to accept coins as payment
(e.g., a merchant).
) - A party who is willing to accept coins as payment
(e.g., a merchant).
- Bank (
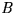 ) - A number of banks will be involved in moving
funds due to conversions between electronic and real money.
) - A number of banks will be involved in moving
funds due to conversions between electronic and real money.
- Certification Authority (
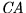 ) - The party who can ``certify''
the public keys of the participants. (In some scenarios, this role
can be played by the Issuer itself.)
) - The party who can ``certify''
the public keys of the participants. (In some scenarios, this role
can be played by the Issuer itself.)
In turn, a coin-holder may play the following roles:
- Coin Purchaser (
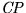 ) - purchases coins from issuer
) - purchases coins from issuer
- Redeemer (
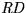 ) - turns coins into real money
) - turns coins into real money
- Payer (
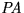 )- customer who pays for goods/services with coins
)- customer who pays for goods/services with coins
- Refresher (
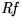 ) - gets new coins for old
) - gets new coins for old
- Changer (
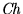 ) - makes change
) - makes change
Further, we make the following distinction amongst participants:
- Registerer (
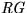 ) - Register a public key at the issuer
) - Register a public key at the issuer
- Enroller (
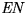 ) - Enroll for a particular role such as
coin purchaser or merchant
) - Enroll for a particular role such as
coin purchaser or merchant
The idea here is that a participant may wish to be able to ``play the game,''
i.e., accept and use coins as a form of payment, without going through
the more elaborate process that enables the purchase or redemption of e-money.
Note that parties and roles are not mutually exclusive.
In VarietyCash all the participants have distinct identities, as well as
public keys. The issuer
has a database listing the identities of all participants, and, for each one,
its public key. This information is entered at the time of registration.
In all transactions directly involving the issuer, there is thus no need
for an external certification authority; however, the design leaves an
option for such a case.
We assume in this extended abstract a unique issuer, thus dispensing with
the presentation of a more elaborate clearing system.



Next: Adversaries and attacks
Up: Model and System Architecture
Previous: Security design goals
Juan A. Garay
7/20/1998
