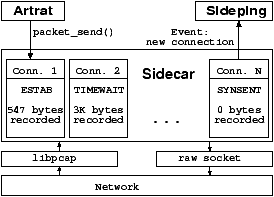
Figure 1: Sidecar is a platform for unobtrusive
measurements that provides an event-driven interface and connection
tracking to higher-level tools, e.g., artrat, sideping.

A Platform for Unobtrusive Measurements on PlanetLabRob Sherwood Neil Spring
|
Abstract: TCP Sidecar is a network measurement platform for injecting probes transparently into externally generated TCP streams. By coupling measurement probes with non-measurement traffic, we are able to obtain measurements behind NATs and firewalls without alerting intrusion detection systems. In this paper, we discuss Sidecar's design and our deployment experience on PlanetLab. We present preliminary results from Sidecar-based tools for RTT estimation (“sideping”) and receiver-side bottleneck location (“artrat”).
Sidecar (Figure 1) is a platform that supports transparently injecting measurement into TCP streams. Probes consist of acknowledgments and replayed data segments, carefully crafted not to interfere with the ongoing TCP connection. Sidecar requires no modification to end-points, requires no firewall rules (unlike Sting [16]), and can run at either end-point of a stream or even in a network middle box. Sidecar's only requirement is that it be on both the forward and reverse paths of a connection. Sidecar probes require an external source of TCP traffic, but the characteristics of the application being instrumented matter little.
Figure 1: Sidecar is a platform for unobtrusive measurements that provides an event-driven interface and connection tracking to higher-level tools, e.g., artrat, sideping.
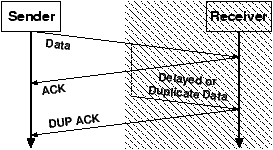
Figure 2: Sender incorrectly assumes (shaded region) that duplicate ACKs are from delayed, reordered, or duplicated packets.

Figure 3: Receiver incorrectly assumes (shaded region) that probes are valid retransmissions from sender due to lost ACK.
Typically, a Sidecar-enabled tool would further modify probes. For example, one could implement a Sidecar traceroute-like [8] topology discovery tool by setting the IP TTL field of the Sidecar probe to 1, and then incrementing until an ACK was received from the end-host. With Sidecar running on a web server, this tool would obtain the path back to any client without out-of-stream packets.2
Figure 4: Reality: Sidecar probes are replayed data packet that generate duplicate ACKs. Probes are transparent to both sender and receiver applications.
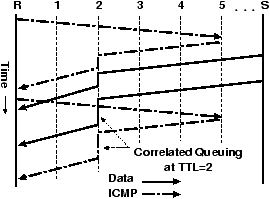
Figure 7: Overview: Artrat correlates congestion and queuing delays to do receiver-side bottleneck location (example: bottleneck from S to R at TTL=2).
We ran artrat on a local network testbed to test the scheme. The testbed consisted of a client connected with a 10Mbps Ethernet card to a 100Mbps network. We ran artrat while the network was idle (Figure 8) and while downloading a 20MB file (Figure 9). When the network was idle, artrat found no significant queuing delay. While the network was in use, artrat successfully found queuing delay on the inbound portion of the 10Mbps link (labeled “1→ R” in Figure 9).
Figure 9: Artrat Experiment: Data Transfer: bottleneck at 1→R, i.e., 10Mbps link. (Data labels as in Figure 8)
This document was translated from LATEX by HEVEA.