
The rsync implementation uses a programming construct referred to as a
process triangle that defines three processes, one on the
source and two on the target (Figure 2).
The generator process runs on the
target and generates the checksums for the target file (![]() ) that get
sent to the sender process (
) that get
sent to the sender process (
![]() ). The sender
scans the source file (
). The sender
scans the source file (![]() ) for the sums it receives and transmits the
results to the receiver process (
) for the sums it receives and transmits the
results to the receiver process (
![]() ). The receiver
applies the delta commands and notifies the generator if a file needs
to be resent (
). The receiver
applies the delta commands and notifies the generator if a file needs
to be resent (
![]() ). The generator and
receiver processes run independently on separate files
concurrently and proceed independently.
). The generator and
receiver processes run independently on separate files
concurrently and proceed independently.
Rsync transmits ADD and COPY commands in the order in which they were detected during a sequential scan of the source file. The target applies the commands in the order received. No destination offsets need to be specified for COPY and ADD commands. The algorithm calculates the destination offset from the previous destination offset and the length of the previous command.
With ip-rsync, the commands undergo a reordering step to facilitate corruption-free, in-place reconstruction. As such, the transmission of the ADD and COPY commands in a non-sequential order requires the explicit specification of a destination offset with each command. The destination offset allows commands to be applied in any order at the target. The extra data in the ip-rsync codeword adds a small overhead to the bandwidth requirements.
Ip-rsync takes the following actions to synchronize a file (the bold text indicate where ip-rsync and rsync differ):
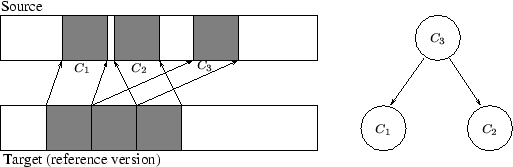 |
In detecting and resolving dependencies, ip-rsync sacrifices some concurrency. The sender conducts an analysis of all COPY commands prior to transmitting any commands to the receiver. This causes ip-rsync to wait until all COPY commands are found and analyzed before transmitting data. Traditional rsync overlaps detecting and transmitting matches by sending data to the receiver immediately. The sender detects dependencies among all COPY commands and waits for the discovery of all commands before reordering.