|

To determine the effectiveness of spoofing attacks in terms of scale we rely on the same publicly-available wifi maps used for analyzing wildfire worms. We attempt to get a rough estimate of the number of access points that hosts on the map can connect to. As we only have access point locations, we add hypothetical hosts within range from each access point. We distribute 1 host per AP and assume a communication range of 60m.
We compute the number of neighboring APs for each host, that is, all APs within range excluding the AP it is directly connected to. We consider only "open" APs that do not use any wireless security protocol, even though the attacker may well be able to crack into WEP-enabled networks using well-known attacks and tools.
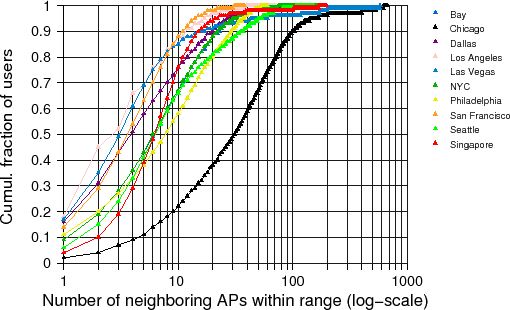
The results for our analysis on 10 different metro areas are shown in Figure 4. We see that in half of the cities 90-99% of all hosts can connect to at least one more neighboring AP; 20-50% of hosts can connect to at least 10 additional APs; and a small but non-negligible number of hosts, as high as 10% in Chicago are within range of more than 100 APs. Unsurprisingly, the results are worse for Chicago, which seems very densely populated, and less so for relatively sparse areas.
Overall, the results confirm our fear that controlling wifi-enabled hosts in densely populated areas can be highly attractive to attackers.