
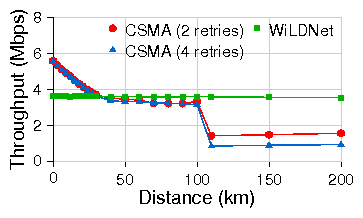
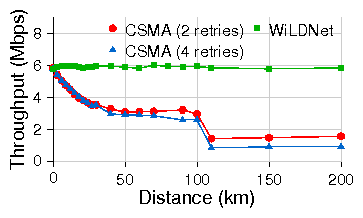
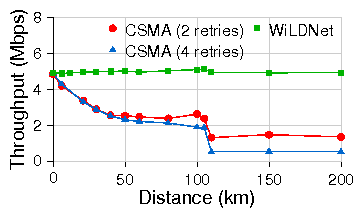
| Link | Dist ance | Loss rates | 802.11 CSMA (Mbps) | WiLDNet (Mbps) | ||
| (km) | (%) | One dir | Both dir | One dir | Both dir | |
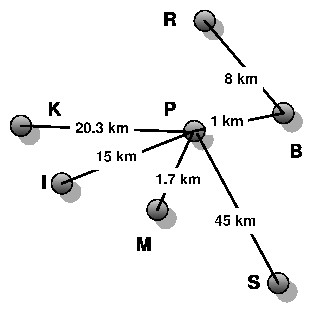
| B-R | 8 | 3.4 | 5.03 (0.02) | 4.95 (0.03) | 3.65 (0.01) | 5.86 (0.05) |
| P-S | 45 | 2.6 | 3.62 (0.20) | 3.52 (0.17) | 3.10 (0.05) | 4.91 (0.05) |
| Ghana | 65 | 1.0 | 2.80 (0.20) | 0.68 (0.39) | 2.98 (0.19) | 5.51 (0.07) |
| Linear setup | 802.11 CSMA (Mbps) | WiLDNet (Mbps) | ||||
| Dir 1 | Dir 2 | Both | Dir 1 | Dir 2 | Both | |
| 2 nodes | 5.74 (0.01) | 5.74 (0.01) | 6.00 (0.01) | 3.56 (0.03) | 3.53 (0.02) | 5.85 (0.07) |
| 3 nodes | 2.60 (0.01) | 2.48 (0.01) | 2.62 (0.01) | 3.12 (0.01) | 3.12 (0.01) | 5.12 (0.03) |
| 4 nodes | 2.23 (0.01) | 2.10 (0.01) | 1.99 (0.02) | 2.95 (0.05) | 2.98 (0.04) | 4.64 (0.24) |
| Description (Mbps) | One | Both |
| direction | directions | |
| Standard TCP: same channel | 2.17 | 2.11 |
| Standard TCP: diff channels | 3.95 | 4.50 |
| WiLD TCP: same channel | 3.12 | 4.86 |
| WiLD TCP: diff channels | 3.14 | 4 |
|
|
|
|