 |

The 1934 edition of the Webster Dictionary contains, after truncation to 8 characters and duplicate removal, 171,395 unique entries. Using standard crypt, the result of hashing every dictionary word under every possible 12-bit salt would fit on a single 9 GB hard disk.
One can do better, however, by storing less than the full output of crypt in a database. The QCrack [12] password cracking program takes exactly this approach. QCrack precomputes a database of common passwords hashed under every salt. Rather than store the full 13 character output of crypt, it further hashes crypt's output down to a single byte. When cracking a password from the dictionary, QCrack uses the database to rule out 255 of every 256 candidate passwords without needing to compute their hashes. A QCrack database of the Webster Dictionary consumes only 670 MB. QCrack could store hashes of approximately 2,350,000 words on a 9 GB hard disk.
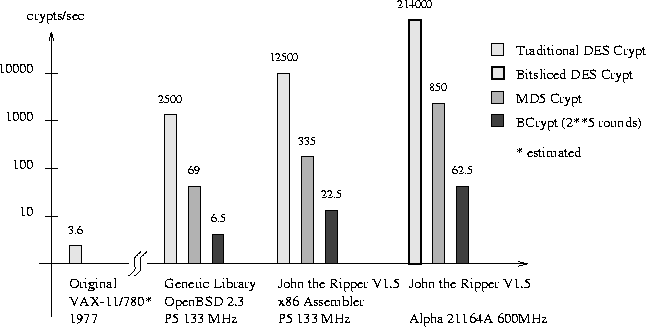
Bcrypt has a large enough salt space to make storing even one bit of information per salt completely intractable. Moreover, the algorithm makes immediate use of the password and salt from the very beginning. Thus, before knowing a target password's salt, there is not even an intermediary state of the algorithm that can be usefully precomputed.