 Notice that the above strategy may
falsely classify benign binaries as malicious. To evaluate the false
positives, we use the following heuristic: we optimistically assume
that all suspicious binaries will eventually be discovered by the
anti-virus vendors. Using the set of suspicious binaries collected
over a month historic period, we re-scan all undetected binaries two
months later (in July, 2007) using the latest virus definitions.
Then, all undetected binaries from the rescanning step are considered
false positives. Overall, our results show that the earlier analysis
is fairly accurate with false positive rates of less than 10%. We
further investigated a number of binaries identified as false
positives and found that a number of popular installers exhibit a
behavior similar to that of drive-by downloads, where the installer
process first runs and then downloads the associated software
package. To minimize the impact of false positives, we created a
white-list of all known benign downloads, and all binaries in the
white-list are exempted from the analysis in this paper.
Notice that the above strategy may
falsely classify benign binaries as malicious. To evaluate the false
positives, we use the following heuristic: we optimistically assume
that all suspicious binaries will eventually be discovered by the
anti-virus vendors. Using the set of suspicious binaries collected
over a month historic period, we re-scan all undetected binaries two
months later (in July, 2007) using the latest virus definitions.
Then, all undetected binaries from the rescanning step are considered
false positives. Overall, our results show that the earlier analysis
is fairly accurate with false positive rates of less than 10%. We
further investigated a number of binaries identified as false
positives and found that a number of popular installers exhibit a
behavior similar to that of drive-by downloads, where the installer
process first runs and then downloads the associated software
package. To minimize the impact of false positives, we created a
white-list of all known benign downloads, and all binaries in the
white-list are exempted from the analysis in this paper.
Of course, we are being overly conservative here as our heuristic does
not account for binaries that are never detected by any anti-virus
engine. However, for our goals, this method produces an upper bound for
the resulting false positives. As an additional benchmark we asked for
direct feedback from anti-virus vendors about the accuracy of the
undetected binaries that we (now) share with them. On average, they
reported about 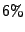 false positives in the shared binaries, which is
within the bounds of our prediction.
false positives in the shared binaries, which is
within the bounds of our prediction.
Niels Provos
2008-05-13

![]() false positives in the shared binaries, which is
within the bounds of our prediction.
false positives in the shared binaries, which is
within the bounds of our prediction.