 A subset of UML diagrams is used to model (an excerpt
of) the procedure that is followed during project trials for delivering
the voting software to the polling stations (See Figure
3).
A subset of UML diagrams is used to model (an excerpt
of) the procedure that is followed during project trials for delivering
the voting software to the polling stations (See Figure
3).
Figure 3:
An example of asset flows
|
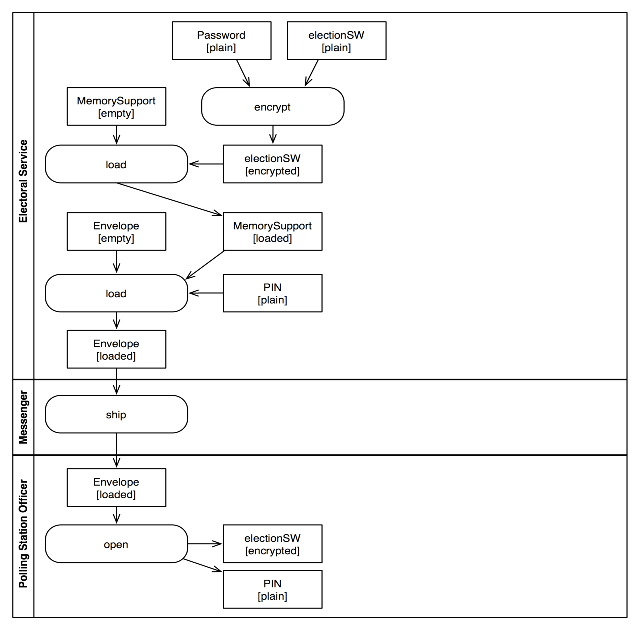 |
The diagram shows how, before the election, the Electoral Office
encrypts the e-voting software and creates a memory support which
contains the final software release. The responsible person at the
Electoral Office
then prepares an envelope
with the PIN code (that it is used to activate the voting functions)
and the memory
support. A messenger (e.g. a police officer) takes the envelope and
delivers it to the polling station, where the polling officers, once
verified that the enveloped is sealed, open it, insert the memory
support in the voting machine, insert the PIN and start the voting
operations.
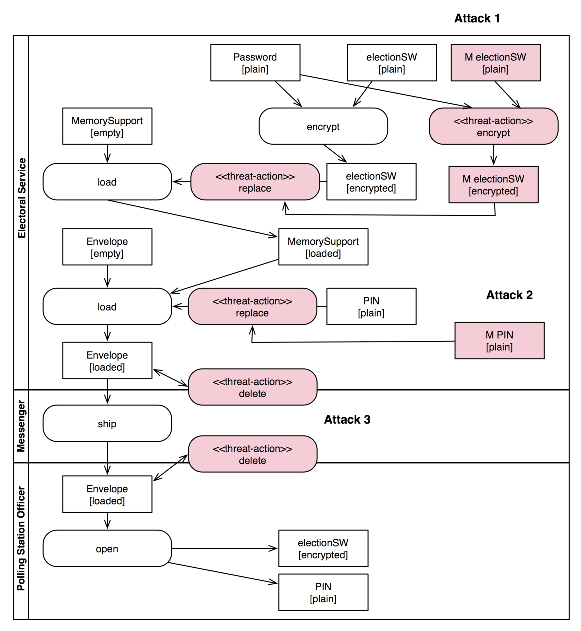
In order to analyze possible threats to this procedure, we inject
threats into the model of the procedures and generate the extended model.
Figure 4 depicts the extended model resulting from the
injection of some delete and replace threat actions in the
example of Figure 3 (threat actions are stereotyped with the
``threat-action'' stereotype and marked in color). Note that the semantics of delete
and replace actions may slightly vary when applied to different kinds of assets.
Figure 4:
An example of extended model
|
 |
komminist
2008-06-30
